Adult
Anonymizers
Chat
Dating
Education
Entertainment
Financial
Gambling
Games
Government*
Health
Humor
IT
Legal
Misc*
News*
Porn
Real estate
Religion
Search engines
Shipping logistics
Shopping*
Social networking
Travel
Unsupported languages*
Webmail
With the exception of the categories marked with an asterisk (*), each of these categories can be modified with exceptions, using the following categories:
Adult
Anonymizers
Chat
Dating
Education
Entertainment
Financial
Gambling
Games
Health
Humor
IT
Legal
News
Porn
Real estate
Religion
Search engine
Shipping Logistics
Shopping
Social networking
Travel
Webmail
The News and the Shopping categories have their own subset of sub-categories for use as exceptions.
News:
Adult
Education
Entertainment
Financial
Government (town of)
Health
IT
Misc
Politics
Porn
Real estates
Sports
Travel
Weather
Shopping:
Adult
Automotive
Beauty
Bedding linen
Boxes packaging
Clothing
Construction
Eyewear
Food grocery
Houseware home appliances
Industrial
IT
Jewelry
Judaica
Medical supplies
Misc
Office school supplies
Porn
Shoes
Textile
Toys
See the exceptions section in the help page for the Category List Rule for more information about exceptions.
URL-Based Categories:
URL-based categories are, essentially, a database of known sites, similar to what standard common filtering systems use. These lists allow us to save processor resources, as the filter does not need to examine the entire content of the page, and only needs to match the URL. This is similar to the URL List rule. The following categories are available:
Adult URLs
Chat URLs
Dating URLs
Entertainment URLs
Filesharing URLs
Financial URLs
Games URLs
Humor URLs
News URLs
Piracy URLs
Religion URLs
Search engine URLs
Social networking URLs
Sites matching those in the URL-based Categories will always return a value of 100% match. The percentage amount is irrelevant for those items, and can be set at anything greater than 0.
URL-based Categories do not allow for subcategory-based exceptions.
Image Alteration Rule
Overview:
Basic Alteration rule:
Basic setup:
Advanced Options
Facial Recognition:
Additional Options:
Stop Processing
Enable Porn, Lingerie, and Human Detection
Apply in Context
Apply Rule all the time
Image Alteration Rule
Overview:
The Image Alteration rule is one of the most powerful rules Livigent offers. It is also one of the most power-consuming rules. All images (unless previously whitelisted) are scanned by the filter, and their content is analyzed. Based on the analysis, the rule’s actions are activated. The Image Alteration rule searches for several types of content in the images, as will be listed below. This rule can be used to prevent access to pornographic images, or other images, which may be considered inappropriate or offensive in an office setting.

Basic Alteration rule:
In its most basic configuration, the filter scans each image for skin tones. Each pixel of the image is analyzed, and a running tally is kept of how much of the image is skin tones. When the filter completes analyzing the image, it compares the results (in percentages of the total image) to the specific rules set up. Two options exist:
Image Alteration will occur at a lower threshold. When the percentage of skin-toned pixels in image reaches this threshold, all skin-toned pixels in the image are replaced by the color preset in the rule.
Image Replacement will usually happen at a higher threshold. When the amount of skin-toned pixels in the images reaches this threshold, the entire image is replaced with a single, solid color, as preset in the rule.
If so desired, Image Alteration can be skipped, by setting the same threshold level to both the Skin Replacement and the Image Replacement options. Once the threshold is reached, the image will be completely replaced.
Basic Setup:
Select “Add new Image alteration rule”.
1. Enter a name for the rule.
2. Select the “Replacement threshold” by entering a number in the box, or by using the slider arrow under the first image.
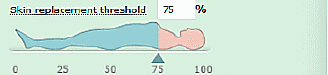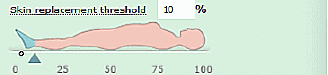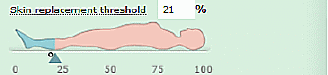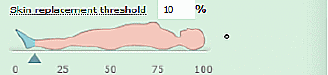
3. Select the color to use when replacing skin tones. All skin tones in altered images will be replaced by that color. You can enter an HTML color code, or click the colored box to open a color chooser.
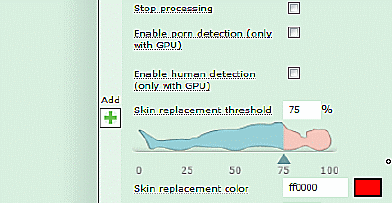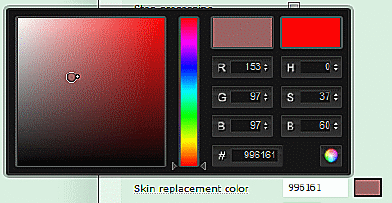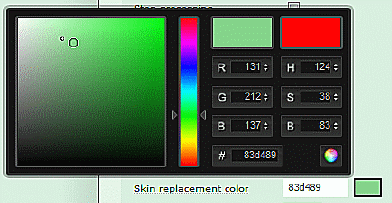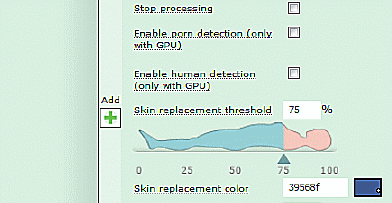
4. Repeat for “Replacement threshold”.
5. Click “Save” to save the rule.
Advanced Options
Facial Recognition:
The Image Alteration rule also allows for better identification of images, by using facial recognition. When Facial Recognition is activated, the filter will process the image, as usual. However, if the image includes faces, the filter will ignore the faces in its calculation of the skin-tone threshold. This allows us to set a different set of thresholds for images with faces, so that filtering can be more intensive for images with faces.
To set up Facial Recognition, check the “Enable face detection” checkbox:
A new section will open, with a second set of threshold and color selectors – one for alteration and one for replacement. Set the desired values and colors as in the basic setup.
Additional Options:
There are several additional options available in this rule:
Stop Processing.
Enable Porn Detection.
Enable Lingerie Detection.
Enable Human Detection.
Apply in Context.
Apply policy/rule all the time.
Stop Processing
Enabling this option will prevent a second Image Alteration rule from processing the image. This is possible if several policies are applied to the same user, and each contains an Image Alteration rule (See {Applying Policies}). Since applying an Image Alteration rule to an image which has been altered already is pointless (it will not find any skin tones), there is no need to waste processor power on it.
Enable Porn, Lingerie, and Human Detection
These two options allow the filter to identify body parts in images, or identify images which contain clearly pornographic content. Lingerie detectionis available only when the Porn detection option is selected. If these options are used, images which are identified as having such content are blocked, with no regard to skintone detection.
These options require a dedicated GPU (Graphics Processing Unit, or a discrete video card) on the machine in order to work. As such, they apply ONLY to full-scale Livigent servers, and do not work on the Livigent device, which does not have such a unit.
Apply in Context
This option allows the rule to apply only in the context of a specific secondary rule, such as a Category List or a URL Pattern rule. If associated with such a rule, the Image Alteration rule will apply only to content identified by those rules (see {Context}).
Apply Rule all the time
Unchecking this box allows you to associate the rule with a particular Timeline, so that it takes effect only during this time. See Timelines for more information about this option.
MIME Type Rule
Overview:
The MIME Type rule is used to allow or block specific file types, based on the MIME Type header sent by the web server. MIME types are used to define the specific type of content being sent, and allow the browser to decide how to act on them (download and display, offer to save, open in an external program, etc.). A general explanation of MIME Types can be found HEREextLink. The official list of MIME Types can be found HEREextLink, and a list that matches file suffixes (.doc, .xlsx, .jpg, etc.), can be found HEREextLink. Using a MIME Type rule allows us to block specific type of content (such as executable files or images) even in sites that have their regular content allowed. When used in connection with a URL list, this allows us to whitelist or blacklist specific content from specific lists of sites.
Basic MIME Type Rule
The basic settings for the MIME Type Rule lets us set various MIME Types, and decide on whether to allow or block these types of files.
Basic Setup:
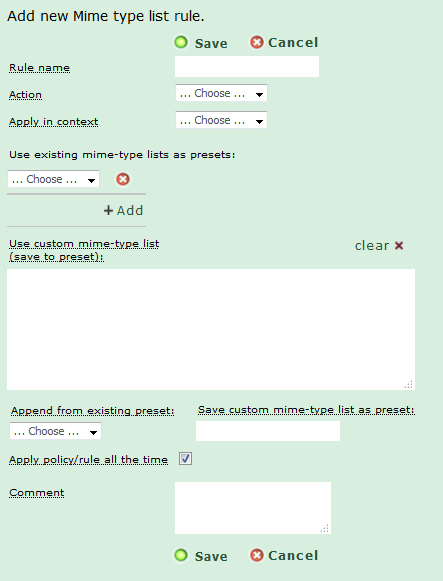
Select “Add new Mime type list rule”.
1. Enter a name for the rule.
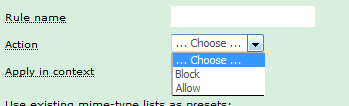
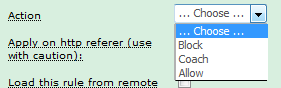
2. Choose the Action to perform when the rule triggers:
3. Enter a list of MIME Types for the rule.
4. Click “Save.”
The list can include any MIME Type. An asterisk (*) can be used as a wildcard to list similar types. Lines beginning with a semicolons (;) are treated as comments.
;This is a comment ;instead of using this list: audio/3gpp audio/ATRAC-X audio/DV audio/mp4 audio/mpeg ;and another 140 types of audio files ;we use: audio/*
Advanced Settings:
Apply in Context
This option allows the rule to apply only in the context of a specific secondary rule, such as a Category List or a URL Pattern rule. If associated with such a rule, the MIME Type rule will apply only to content identified by those rules (see {Context}).
Save/Use custom presets:
Previously created lists can be saved as presets, for use with other directly entered lists. In addition, Livigent comes with several MIME Type preset lists, for the following most common MIME Types:
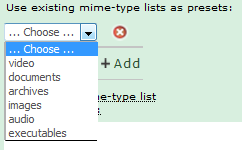
To save a new preset, create a list, following the rules for list creation. Then, give it a preset name:
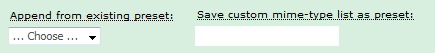
Save the list.
In any subsequent lists, you can select the presets from one of the two available dropdown lists:
The first dropdown includes the contents of the preset list as-is. The preset list contents do not show in the list.
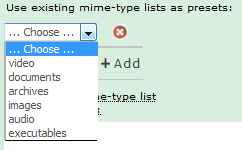
Multiple presets, if such exist, can be used in a list. To use more than one preset, click the “Add” button in the “Use existing URL pattern lists as presets” section to add more lists:
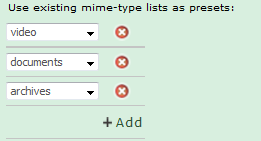
To remove presets from a list, click the DeviceManual-Button_X button next to the preset you want to delete.
The second list appends the contents of the preset to the current contents of the list.
The list can then be edited as needed. Any changes made there do not affect the preset or other lists that use it.
Note:
Currently, there is no method available to delete preset lists. If you’ve created such presets, and want to delete them, contact Livigent Support.
Apply Rule all the time
Unchecking this box allows you to associate the rule with a particular Timeline, so that it takes effect only during this time. See Timelines for more information about this option.
URL List Syntax
Overview:
There are three syntax forms for list entries: Regular Expressions, Wildcard entries, and a specialized Domain Name entry. In addition, comment lines can also be included in the list, to provide notes on content or to disable a specific pattern temporarily. The list can be set up to contain global content (applicable to all users) as well as user-specific content, which applies only to a specific user.
Formatting:
Comments
To mark a line as a comment, begin the line with a semi-colon (;). The entire line will be ignored.
;this is a comment line
Regular Expressions:
Regular Expression (RegExp) entries are compared with the entire URL, including any form data sent via the GET method (e.g. a Google Search link). If the URL or part of it matches the pattern, the action for the rule is preformed.
To be treated as Regular Expressions, the line must begin with the percent sign (%). Livigent uses the POSIX RegExp syntax. For a quick review of the POSIX syntax, see here and here.
%^http(s)?://[A-Za-z0-9\._-]*mail[0-9]{0,3}\.[A-Za-z0-9\._-]*\.[A-Za-z]{2,4}/ This expression searches for URLs that contain the word “mail” within the domain name only, as a way of identifying web-based email systems.
Wildcard Entry:
Wildcard entries are compared with the entire URL, including any form data sent via the GET method (e.g. a Google Search link). If the URL or part of it matches the pattern, the action for the rule is preformed.
Wildcard entries use an asterisk (*) to replace characters. As in standard wildcard notation, an asterisk will replace one or more characters; usage of the asterisk requires at least one character in that position. Multiple asterisks can be used in a line, with other content in between.
Protocol descriptors (e.g. “http://”) are not needed, they are implicitly assumed. Port directives (:xxxx) must be included.
*.mail.com*
Will match:
It will not match:
mail.com
Will match:
It will not match:
*mail.com*
Will match:
It will not match:
All of the above examples will not match:
When using this notation, it is extremely important to remember that a trailing asterisk is usually required in most cases. The only exception is when entering a full resource name (such as a specific HTML page or an image). If the trailing asterisk is missing, the match will most likely fail.
*.google.com
Will not yield any useful results. All this matches to is a URL which ends in google.com. Therefore, any resources, such as the images, scripts, and, in most cases, the entire page content, will not be matched.
It is possible to use more than one asterisk in the pattern. For each use, it will match one or more characters. This is useful for matching multiple versions of a particular URL, without resorting to Regular Expressions:
*.google.co*/search*
will match most Google search pages, regardless of the specific country format. Thus, all of the following formats will be matched:
Domain Notation:
A special Domain Name syntax is also available. If the entire domain is to be matched, enter the domain name preceded by a plus (+) sign. When using this format, wildcards and other directory-level symbols cannot be used. This format allows us to specify an entire domain, without resorting to multiple wildcard notation needed to cover all possible formats of the domain, without allowing others.
To match the domain “mail.com”, including the format “www.mail.com”, a sub-domain “images.mail.com”, but excluding “gmail.com” or “mywebmail.com”, we’d use the following Wildcard notation:
*.mail.com* mail.com*
Instead of this, we can use the simple notation:
+mail.com
This notation cannot be used to match a single sub-domain. It can only match a full domain. It will match sectioned Top-Level Domain endings (such as co.il, or ny.us).
+mail.yahoo.com - NOT Valid! Multi-user lists:
A specific formatting of the URL list allows it to apply different lists to different users. This allows the Filter Manager to utilize the same list for different users, allowing more efficiency in creating policies. One standard policy can be created for multiple users, with the only difference being the specific URL list for each user. Without this option, such a task would require creating a separate policy for each user.
The syntax for a multi-user list is the same as for a regular list. The list is divided into sections, using the “@” symbol, followed by the user’s name. All list entries from that point and on will apply to that particular user, until a new line beginning with “@” is reached.
*.foo.com* *.bar.net* +jedi.org @user1 *.example.com* @user2 mytest.net* +sith.mil
All users will have access to *.foo.com*, *.bar.net*, and the entire jedi.org domain. In addition, user1 (and only user1) will have access to *.example.com*, and user2 (and only user2) will have access to mytest.net*, and the entire sith.mil domain.
URL List Syntax
Overview:
The URL Pattern List Rule allows you to save a list of URLs, in various formats, and either allow or deny access to these addresses. This is done without checking the content of the page. If the address (or parts of it) matches an entry on the list, the action is taken. This allows us to block sites that are known as problematic, but are crafted in such ways that the content filter does not recognize them, or sites we don’t want the filter checking over and over, as we know they are bad. This also allows us to handle false-positives, or to allow sites that would otherwise be blocked by a category filter. This can also allow us to have the Image Alteration Filter run only on a specific set of sites, or prevent it from affecting them.
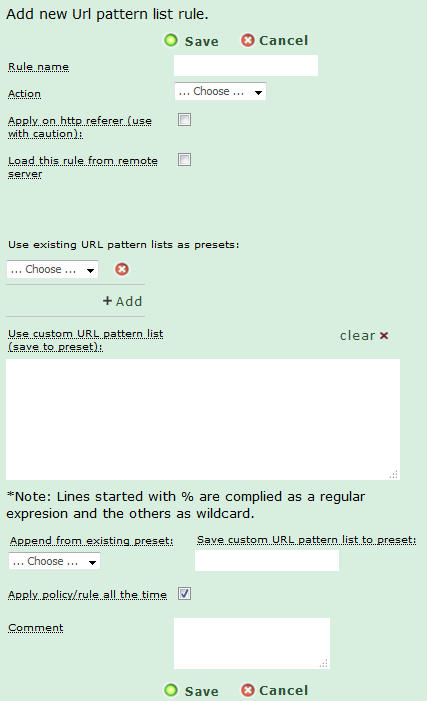
Basic URL List Rule:
The basic format of the rule allows us to directly enter URLs or parts thereof, as well as Regular Expressions (RegExp) functions that can increase the flexibility of the list. Each list can be set up for only one of three actions:
The syntax for a multi-user list is the same as for a regular list. The list is divided into sections, using the “@” symbol, followed by the user’s name. All list entries from that point and on will apply to that particular user, until a new line beginning with “@” is reached.
Basic setup:
Select “Add New URL Pattern List Rule.”
2. Choose the Action to perform when the rule triggers (As explained above):
3. Enter a list of URLs for the rule.
Advanced Settings:
Save/Use custom presets:
Directly entered lists (not remote lists) can be saved as presets, for reuse with other directly entered lists.
To save a new preset, create a list, following the rules for list creation. Then, give it a preset name:
Save the list.
In any subsequent lists, you can select the presets from one of the two available dropdown lists.
The first dropdown references the contents of the preset list as-is. The preset list contents do not show in the list.
Multiple presets, if such exist, can be used in a list. To use more than one preset, click the “Add” button in the “Use existing URL pattern lists as presets” section to add more lists:
To remove presets from a list, click the ![]() button next to the preset you want to delete.
button next to the preset you want to delete.
The second dropdown adds the contents of the preset to the current contents of the list.
The list can then be edited as needed. Any changes made there do not affect the preset or other lists that use it.
Note:
Currently, there is no method available to delete preset lists. If you’ve created such presets, and want to delete them, contact Livigent Support.
Apply on http referrer.
Normally, the pattern list will test each requested resource to match its URL with the list. When this option is selected, and the filter action is “allow” or “coach”, allowed content will include all resources referenced by the allowed URL.
The list contains the line *.example.com*, and is set to allow matched items.
The page at www.example.com/index.htm calls for an image located at www.sampleresources.com/images/image1.jpg, and for an inline embedded page (iframe) from www.sampleresources.com/content/embed.html.
If “Apply on http referrer” is not enabled, the image resource will be subject to all the rules included in the user’s policy. This means that Image Alteration rules will apply to the image, Category List rules will apply to the embedded frame, and they may be altered or completely blocked. This is especially relevant when restricting a user to a specific list of URLs (a whitelist policy). To allow those items, they would have to be explicitly specified in the list. However, this will make the resources always available, and they can be accessed directly as well.
If “Apply on http referrer” is enabled, the resources do not have to be explicitly included in the list, and will be available to a page at example.com. If called directly, or by a page not on this list, the resources will still be subject to the filter rules in the policy.
WARNING:
Use this option with extreme caution. Allowing on http referral means that you have no real control over what becomes allowed. Once a URL is included in the list, any resource it calls will be allowed. This includes content from websites which you would, perhaps, not wish to allow. If you need to include resources that reference also unwanted content, use two URL Lists – 1 with this option checked, and one with it disabled.
Load this rule from remote server:
This option allows storing the list at a remote location, rather than entering it in the Livigent device. Storing the lists on a remote server has several advantages:
To have Livigent obtain the list from a different location, check the “Load this rule from remote server” checkbox.
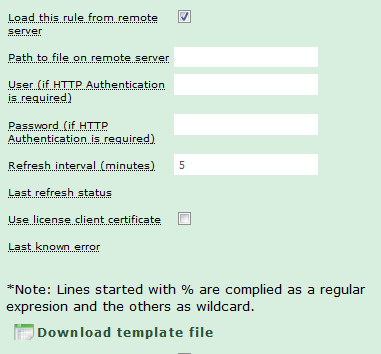
Only one option is required: The address of the remote list. This can be a specific file (text-based), or a call to a remote server, which will generate the text data. Enter this information in the “Path to file on remote server” line.
Livigent can negotiate HTTP authentication on the remote server, if it is set up. Enter the username and password in the “User” and “Password” boxes. Livigent will then make the request in the format http(s)://{user}:{password}@{remoteaddress}.
IMPORTANT! HTTP authentication passes the log-in credentials in plain text. This information can be snooped out of the HTTP requests. Do not rely exclusively on HTTP authentication to protect access. To protect your data properly, remote servers should be firewalled to prevent access from machines other than the Livigent device, or access should be protected with authentication and an encrypted (SSL) connection.
You can set how often Livigent polls the remote server for updates. The default is 5 minutes. Do not set extremely short intervals, to minimize load on the remote server. This is especially true if you have a large number of very large lists, or if your connection to the remote server is slow, as this can cause loopbacks when the list is polled again before it finished downloading. Saving the rule performs an immediate update, regardless of the interval set.
To see a very basic sample file with sample list syntax, click the “Download template file” link.
Once the rule has been saved, and updates have happened, edit the rule again to see information about the most recent update, and to check the current list:
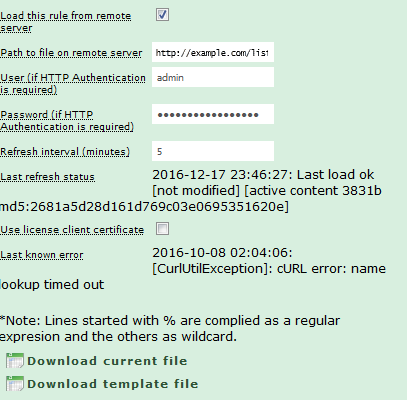
The “Last Refresh Status” shows the last time the file was downloaded from the remote server, and the action taken. If the newly downloaded list had no changes, the information will state “[not modified]”. If the last update contained new information, the “[not modified]” statement will not show. The rest of the information is the actual size of the data loaded, in bytes, and an MD5 checksum of the data, so you can verify that the data downloaded to the server matches with what you actually have.
If any errors have occured in the retrieval process, the error will be shown in the “Last known error” section. Note that the existance of content there does NOT indicate an error exists now. Look at the date shown there and compare it to the latest good update time shown in the status, to see if the error is current or not
Click on the “Download current file” link to download a text file with the current active list. Note that this is not necessarily the same as the most recently downloaded list. If Livigent encounters an error in processing the new data, the previous data will be used, and this is what will be shown in the retrieved file.
Unchecking this box allows you to associate the rule with a particular Timeline, so that it takes effect only during this time. See Timelines for more information about this option.